Unveiling I-Soon
Unveiling I-Soon
This blog reveals how I-Soon, a company collaborating with key Chinese government agencies, is involved in attacking governments, democracy groups, and other entities worldwide. It provides a unique insight into the operations of such companies, which operate under government directives and compete to hack targets by developing their own zero-day exploits. Furthermore, it delves into China's covert cyber campaigns, shedding light on trends such as the increase in zero-day exploits being exploited by state-sponsored hackers, as even observed by Microsoft
I-SOON

I-Soon, also known as Anxun (Shanghai Anxun Information Technology Co.), is a cybersecurity firm founded in 2010. which offers offers information technology security consulting services, including Risk assessments, Firewall/penetration testing, APT attack prevention . On Feburary 16th a I-SOON github repository containing lots of documents and Wechat messages between the employees, employees discussing zero-day vulnerabilities were found. I-Soon was already been suied for i-SOON allegedly being associated with the Chinese state hacking operation APT41.
The repository contained many details about the i-soon operations from 0-days, custom made hacking devices to employees complaining about low pay. The repository also contained a list of victims which they have attacked and breached over the time. I-soon targetted from medicare hospital to different government entities of Malaysia, Mongolia, Nepal, India, Kazakhstan, Egypt, Cambodia, Pakistan and Thailand.
- Ministry of Foreign Affairs Malaysia
- Police station Mongolia
- Ministry of Foreign Affairs Mongolia
- Indian immigration India
- Punjab provincial counter -terrorism center post data Pakistan
- National Intelligence Agency Thailand
- Ministry of Public Security Mongolia
- Government network Nigeria
Tools
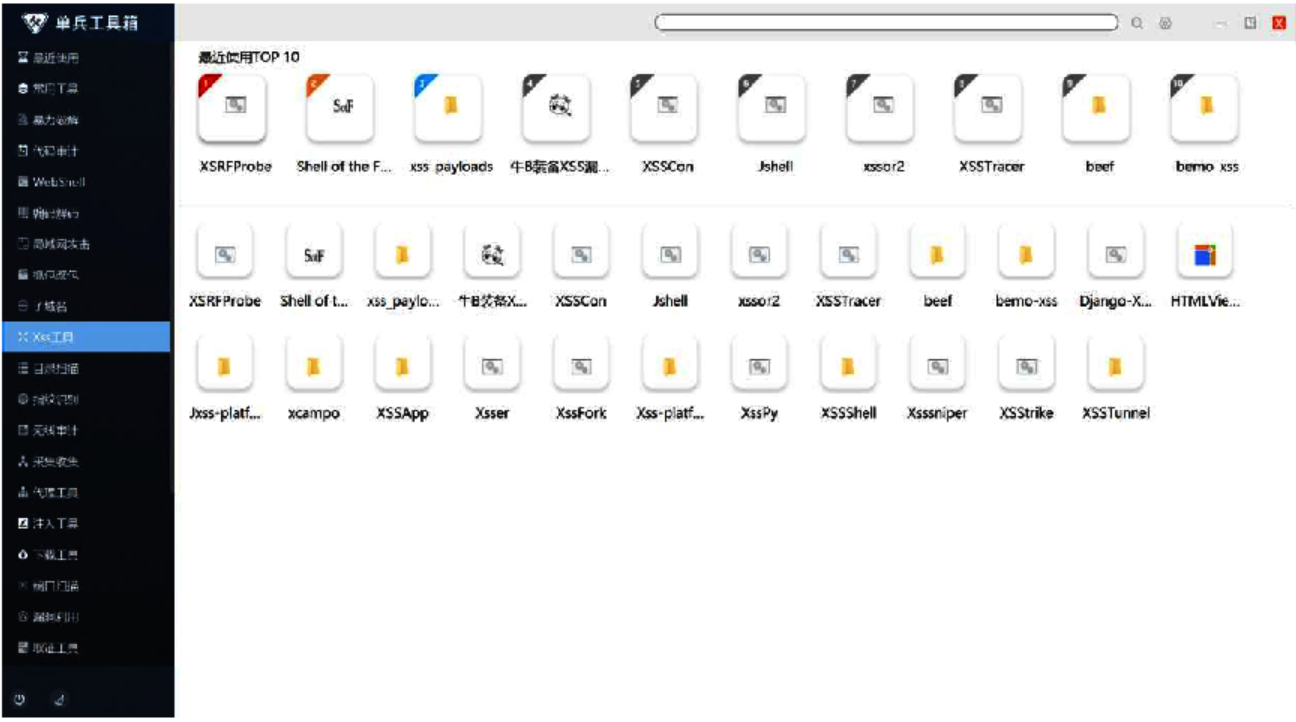
They also developed an advanced intelligence and attack surface tool used by Chinese nation state threat actors known as Single Soldier Toolbox
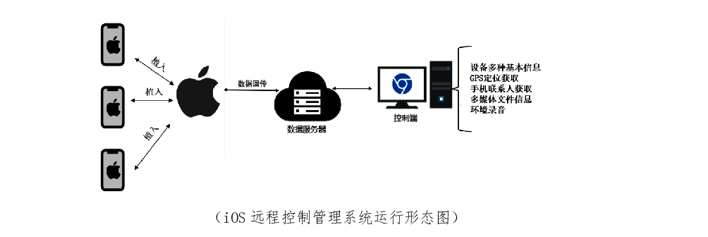
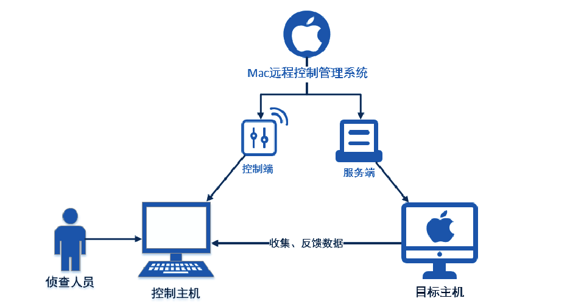
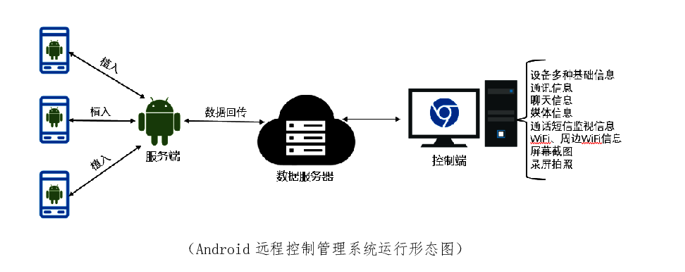
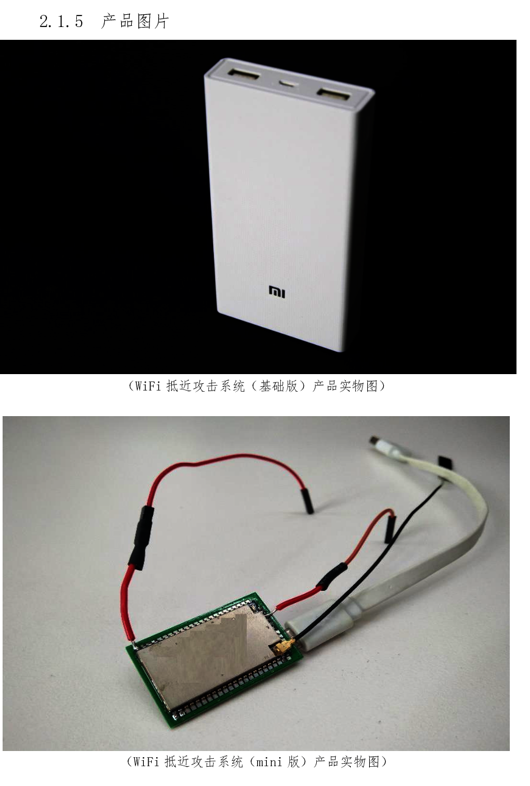 I-SOON created advanced spyware capable of attacking Windows, Macs, iPhones, and Android gadgets. i-SOON's toolkit also encompasses tools for hardware hacking, such as devices for eavesdropping and equipment designed to break into Wi-Fi networks.
I-SOON created advanced spyware capable of attacking Windows, Macs, iPhones, and Android gadgets. i-SOON's toolkit also encompasses tools for hardware hacking, such as devices for eavesdropping and equipment designed to break into Wi-Fi networks.
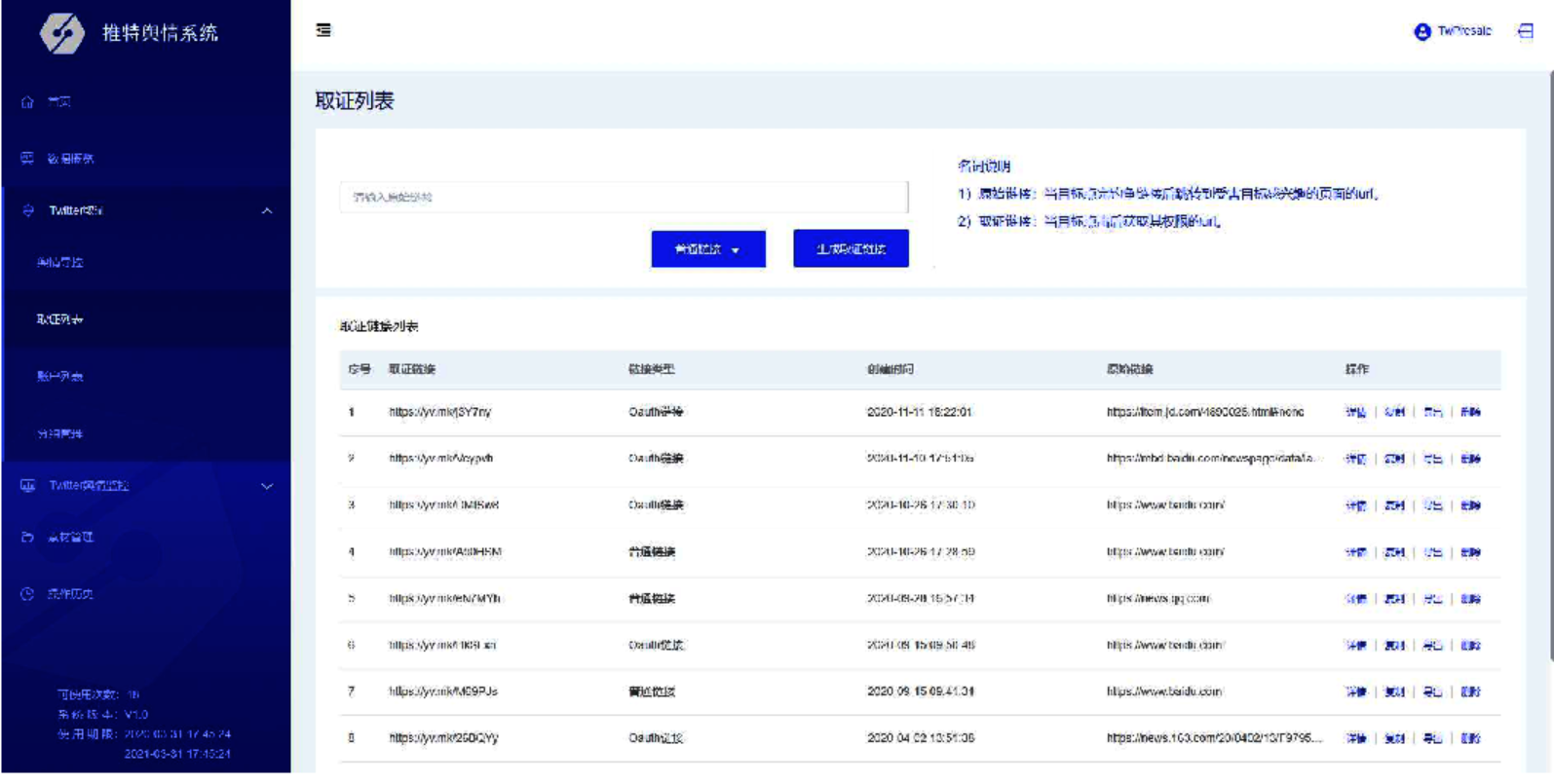 I-soon also developed a Twitter Suspicious Monitoring System
I-soon also developed a Twitter Suspicious Monitoring System
The chats also revealed how chinese government uses Tifanu Cup to get new vulnerablities that were found during the contest and how systematically collected by the Ministry of Public Safety. These are then selectively distributed to provinces known for their strong cyber capabilities, and eventually, to contractors for operational use. where the POC are turned into actual Exploits.
To know more about the I-SOON